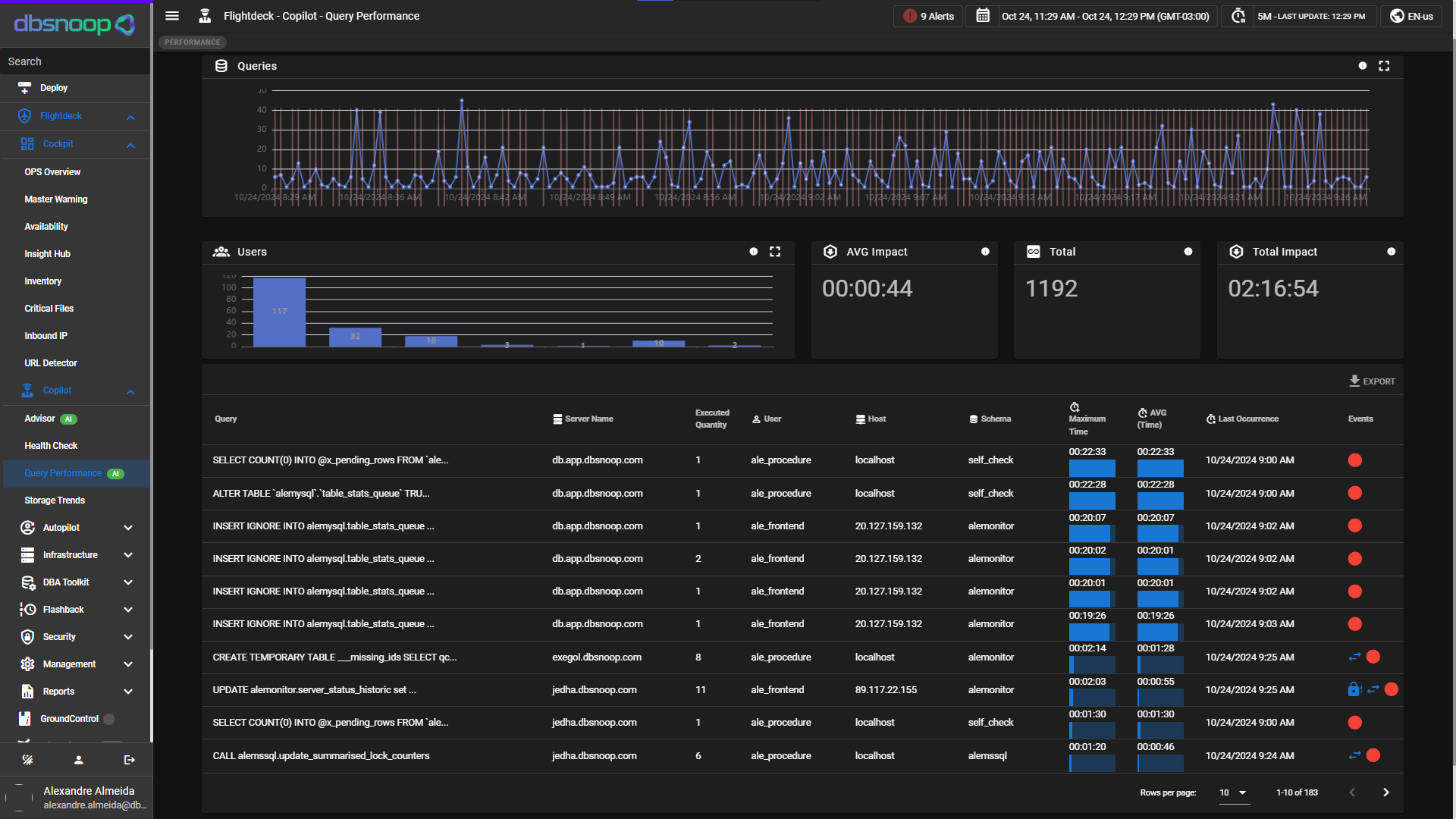
In today's rapidly evolving digital landscape, the security of applications has become a top priority for organizations of all sizes. With the increase in cyberattacks and data breaches, ensuring that applications remain secure and compliant with regulatory standards is essential. Security auditing plays a critical role in this process. By continuously monitoring, detecting, and reporting on potential security risks, businesses can safeguard their applications against vulnerabilities and unauthorized access. In this article, we explore the importance of security auditing in modern applications and how it helps organizations maintain robust security practices.
The Role of Security Auditing in Modern Applications
Security auditing refers to the process of reviewing and analyzing an application's security posture, including its architecture, coding practices, and infrastructure, to identify weaknesses that could be exploited by attackers. In modern applications, which are often complex and built on a range of technologies such as microservices, cloud platforms, and third-party integrations, security auditing is more critical than ever. It involves a comprehensive assessment of security controls, access management, data protection protocols, and compliance measures. Regular security audits ensure that applications are resilient against evolving threats and help organizations mitigate risks before they become significant issues.
Continuous Monitoring for Threats and Vulnerabilities
One of the core components of security auditing in modern applications is continuous monitoring. With the increasing sophistication of cyberattacks, it is no longer enough to rely on periodic security checks. Organizations must continuously monitor their applications for any signs of potential threats or vulnerabilities. This includes monitoring network traffic, user activity, application logs, and security configurations. By implementing real-time monitoring, security teams can detect unusual patterns or suspicious behavior that could indicate a security breach, such as unauthorized access or data exfiltration attempts. Continuous monitoring ensures that security teams can act quickly and address issues before they escalate into full-blown attacks.
Detecting Security Threats with Advanced Tools
Security auditing in modern apps relies on advanced detection tools that help identify potential threats and vulnerabilities in real-time. These tools are designed to scan for known security weaknesses, such as outdated software components, misconfigurations, and unpatched security flaws. They also use machine learning and AI-based techniques to identify emerging threats that might not yet have been recognized by traditional security measures. Vulnerability scanning tools, intrusion detection systems (IDS), and security information and event management (SIEM) platforms are often employed to detect abnormal activity and potential risks. By integrating these tools into the development and operational environments, organizations can detect threats as they occur and take immediate action to mitigate them.
Identifying Compliance Gaps and Regulatory Violations
Another key aspect of security auditing is ensuring that applications comply with relevant industry regulations and standards. In many sectors, such as finance, healthcare, and e-commerce, there are strict rules governing the handling of sensitive data, including how it is stored, transmitted, and protected. Security audits help organizations assess whether their applications meet the requirements of frameworks like GDPR, HIPAA, PCI-DSS, and SOC 2. Auditors review data protection measures, access controls, and encryption practices to ensure that applications are in compliance with these regulations. Identifying and addressing compliance gaps is crucial to avoid hefty fines, legal liabilities, and reputational damage that can arise from non-compliance.
Reporting Security Findings and Providing Actionable Insights
Once a security audit has been conducted, the next step is reporting the findings and providing actionable insights. Clear and detailed reporting is essential for security teams to understand the scope and severity of any vulnerabilities or threats identified during the audit. A well-structured report will highlight areas of weakness, categorize the risks, and provide recommendations for remediation. These reports are typically shared with both technical teams and executive leadership to ensure that the necessary resources are allocated to address the issues. Additionally, security auditing tools often provide dashboards and visualizations to help track vulnerabilities over time and monitor the progress of mitigation efforts.
The Importance of Remediation and Continuous Improvement
A successful security audit is not just about identifying threats—it is also about taking action to address them. After receiving the audit report, organizations must prioritize remediation efforts based on the severity of the risks identified. This may involve patching vulnerabilities, updating software, reconfiguring security settings, or implementing stronger access controls. However, security auditing is an ongoing process. As new threats emerge and applications evolve, security teams must continue to monitor, audit, and improve their security measures. Continuous improvement helps ensure that applications stay ahead of potential risks and maintain a high level of protection against cyberattacks.
Integrating Security Auditing into the DevOps Lifecycle
In modern app development, the integration of security practices into the DevOps lifecycle, known as DevSecOps, is becoming increasingly important. By embedding security auditing tools and practices directly into the development and deployment pipelines, organizations can identify and address security vulnerabilities early in the development process. This proactive approach reduces the risk of security flaws being introduced into production environments and ensures that security is a key consideration at every stage of the software development lifecycle. Security auditing in a DevSecOps context allows for continuous feedback, faster detection of issues, and more efficient remediation, leading to more secure applications in the long term.
Conclusion
Security auditing is an essential practice for maintaining the integrity and security of modern applications. By monitoring applications continuously, detecting potential threats with advanced tools, and ensuring compliance with regulations, organizations can safeguard their apps from vulnerabilities and breaches. Reporting security findings and taking prompt action to remediate any identified issues further strengthens security posture. Integrating security auditing into the DevOps lifecycle ensures that security is maintained throughout the entire development process, ultimately leading to more secure, reliable, and compliant applications. In today’s increasingly digital world, regular security audits are crucial for protecting sensitive data, maintaining trust, and mitigating risks before they can cause significant harm.

































Comments